Secure: Security Software Redesign
My Role: Research, Workshop Facilitation, Synthesis, Audit, Design.
Design tools: Figma & Whimsical.
Duration: 8 months.
Team: 4 designers, 1 project manager, vast team of engineers.
ABOUT Secure
Secure (not a real name) is a Fortune 500 company (but the company is real) in Security and Maintenance Sector. They operate globally and have been one of the major leaders in this space. Secure has a huge value offering for it’s clients, but is currently losing ground to new competitors.
Secure has an old legacy software, that is a foundation to a few products combined under one umbrella, that has been frankensteined for over a decade: new features were smashed on top of each other; all requests from customers were added; errors and confusion had a band aid fix, that temporarily fixed one issue while simultaneously created another.
Secure’s engineering driven strategy led to a very complex, hard to use product.
Project overview
Problem: 80% of Secure customers use 20 % of their features. Mainly because there are a lot of features, nested within one another, hidden from users and not easy to learn.
Why is it important: Secure is a fortune 500 company in security and surveillance sector, with big value proposition, but losing customers to new competitors. Because new products offer simple design, clarity and ease of training for new hires, ease of maintenance and perceived higher quality.
Solution: Our team has designed a 2 full day workshop to unpack the most valuable, high impact features to include in the redesign of the legacy software. We preserved the branding of Secure but designed a new look and feel following the Material Design Guidlines. We interviewed their customers to confirm the most valuable features and to learn more about their use cases. The MVP software included: custom search and filtering; tagging; creation and assigning of events; camera controls; staff management
Design process
Discover: Interviews
We wanted to understand what is the main problem from different groups to gather their perspectives. We conducted rounds of interviews with the leadership, core product team, and the main customers of the Secure.
These are the patterns we observed:
In spite of offering every imaginable and useful feature, Secure would be losing to new competitors, that offering a lot less to their customers, but doing a great job at those few things
Only 20 % of features are used by Secure’s customers.
Users are not aware of the 80% of features of Secure’s surveillance product.
Secure internal teams work in silos and are not aware of issues, and priorities of other teams. There is no alignment on the top priorities and direction within the management at Secure.
Engineering driven decisions created extremely cumbersome workflows.
3rd party integrations are causing errors and crashes in software.
Discover: Synthesis
We synthesized those patterns and visualized them in Mural.
Discovery workshop
We gathered two main teams, servicing two core products that Secure is offering for two full days of workshops.
Activities that helped us distill vague requests into prioritized plan:
Build Empathy Map Canvas
Co-create Persona and User Stories
Create Future State User Journey
Map the features
Prioritize V1 and V2 features
DEFINE: WHAT ARE THE MAIN USER GROUPS?
Who will be using the product?
There are 4 main user groups for this product:
Security Systems Manager
Security Officer
Receptionist/SOC Operator
Security Guard in SOC 👉
DEFINE: JOURNEY MAP
What Journey does Jack go through while using the product?
What does he do?
What does he feel at each step of the journey?
What are some of his daily tasks?
What does he think when he performs those tasks?
What are his pain points?
How Might We address them?
DEFINE: FEATURES PRIORITIZATION
What features bring the most value to Jack?
What security functions of the software are essential for Jack to perform his duties?
Features were prioritized in the 2 day workshop.
Live monitoring with smart detection
Intelligent alert systems that bring people’s attention to the most urgent situations
Ability to assign clearances in custom efficient ways that work for different needs within his company
DEFINE: User Flow
What tasks does Jack perform day to day?
Search for camera to assess emergency situations
Create and save a new layout
Prepare and send incident reports
Restrict access
Add a new camera to the layout
Add new camera from saved views
What are Jack’s pain points?
The points highlighted are the ones we are going to look at in this case study. Too many cameras to monitor at the same time
Hard to notice urgent notifications in the stream of live data
No feedback on the loss of video
Hard to locate device or a person quickly
Cumbersome Reporting
Design: How might we resolve these pain points?
Device finder that is essentially a filter:
Omnipresent as an expendable floater on every screen
Updates results dynamically
Structures search options to narrow down search results
Allows to save presets for common searches
Out of the box reporting templates
Ability to save report to dashboard
Ability to re-run last top 5 reports
Intuitive data visualization
Design: Exploring potential solutions
I have started in low fidelity utilizing Figma UI kit
Leveling up the fidelity of the design
We used current Secure branding as guide in high fidelity design - to make sure the application blends with the current suit of applications. We have utilized Material Design as a guide and inspiration.
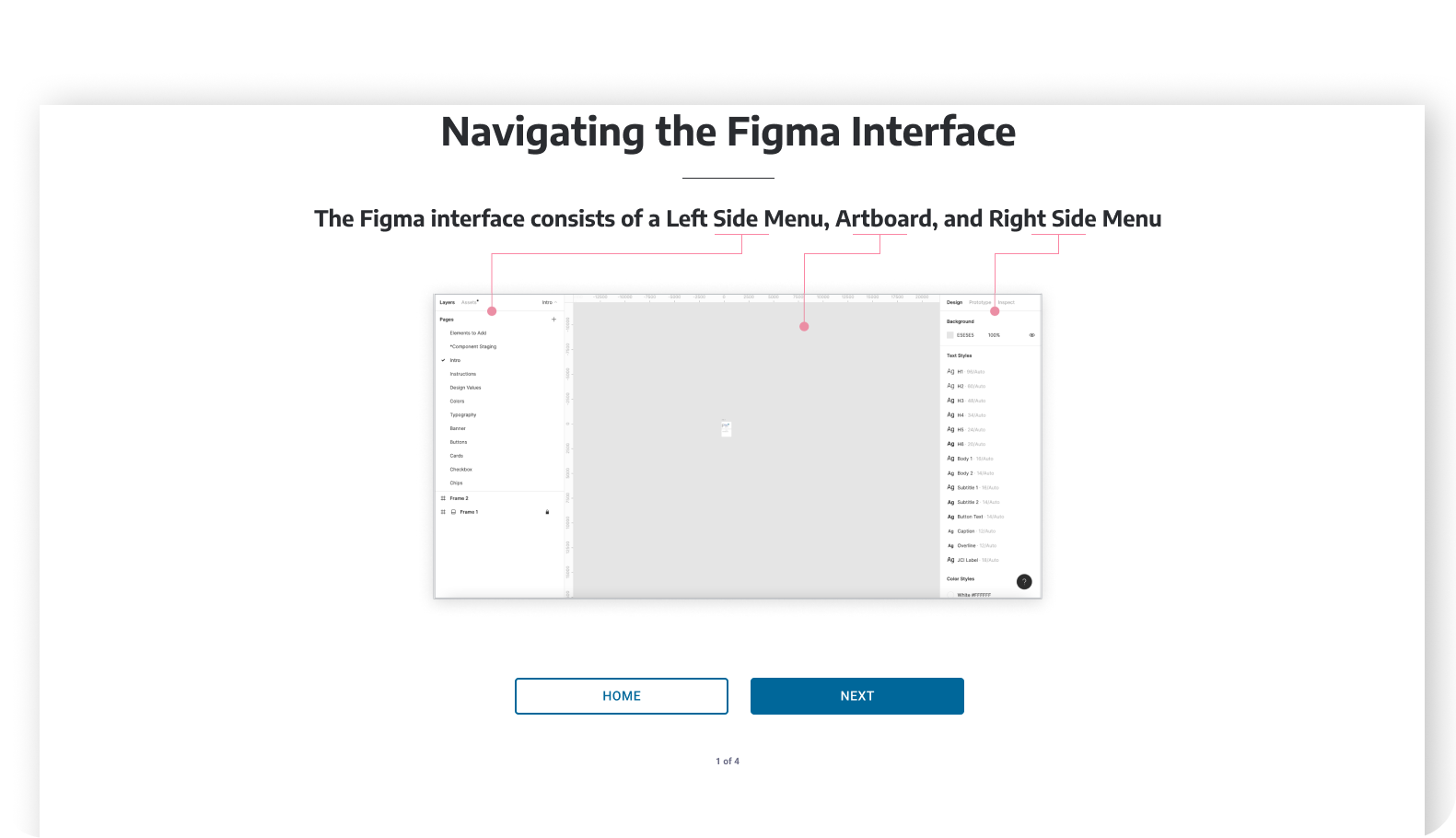
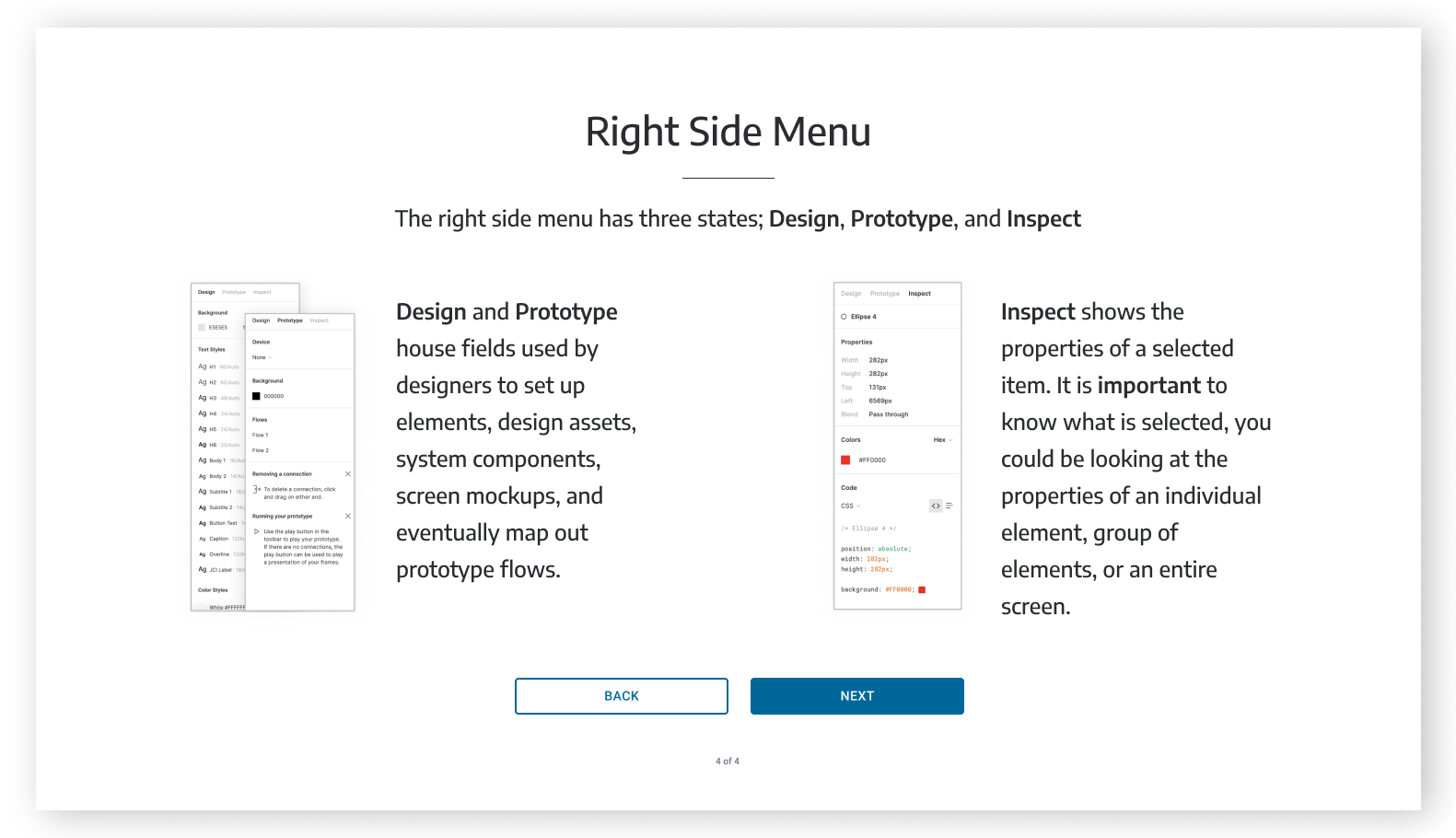
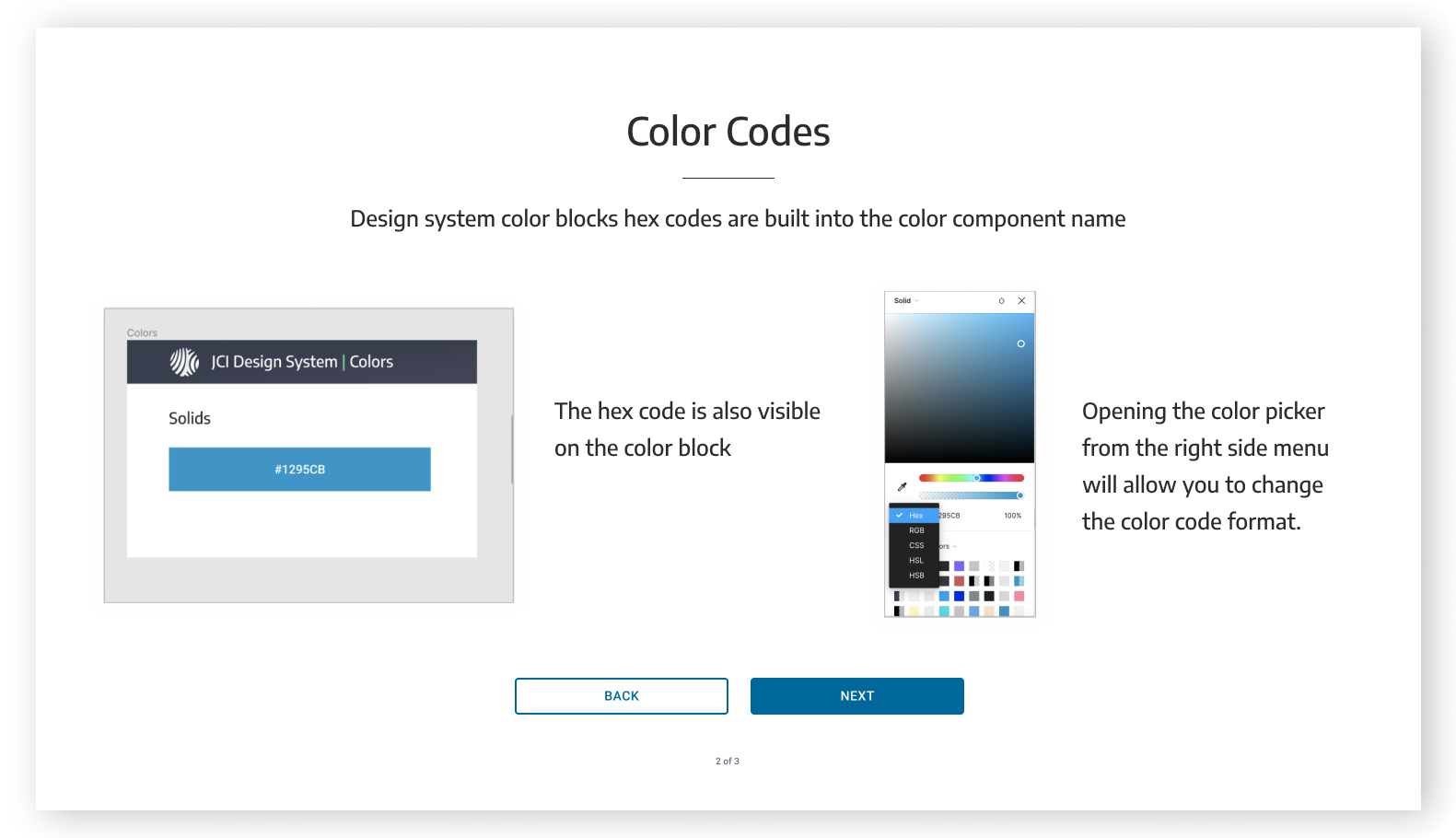
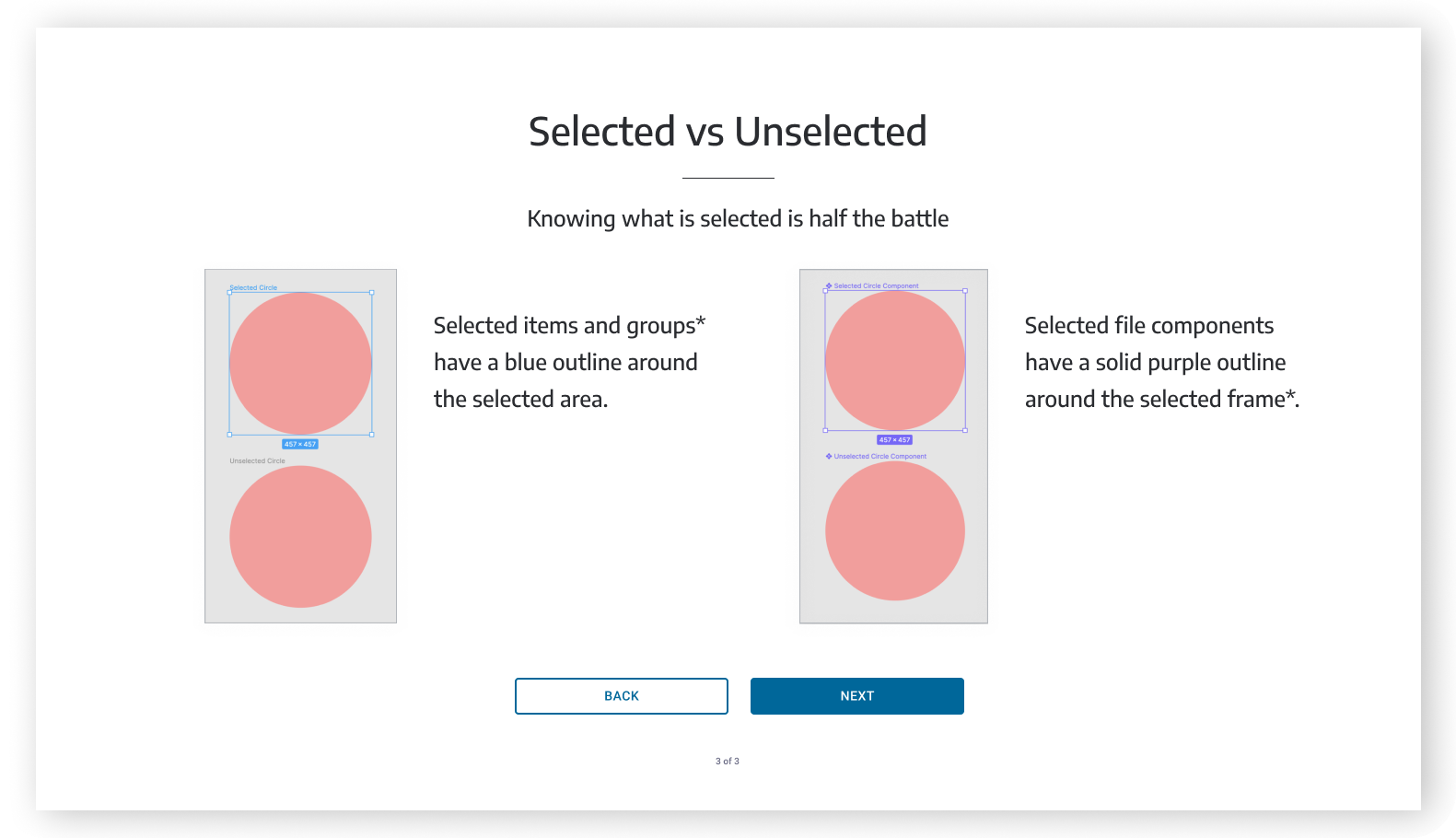
DESIGN SYSTEM
In this project we quickly understood that Secure is struggling with design and product development for many reasons, one of them being lack of system and thus consistency. We worked on a design system based on the project that we did for them - that captures the new visual language, components and patterns for Secure.








WHAT WENT WELL WITH THE PROJECT
Core 5 features were designed and implemented by the team, 10+ features were handed off for future development
Working with our strong design team secured buy-in from the leadership on hiring internal designer for their core team
Secure’s two siloed product teams aligned on the direction and the priorities for a new product vision
WHAT DIDN’T GO SO WELL IN THE PROJECT
Client had growing pains with adapting the design first approach. Towards the end of the project the working process came down to staff augmentation which is a loss of opportunity for our contribution and expertise.
Lost opportunity to collaborate with Secure’s engineers. Which caused implementing the designs not exactly as intended and some solutions weren’t our designs and lacked intended usability.
Our solutions weren’t tested with actual users.
KEY OUTCOMES
New visual language and desired component behavior captured in the Design system
Simplified and greatly improved user experience in core features: finding devices; creating schedules; camera controls; tagging; staff scheduling
New iconography and data visualization integration
Positive feedback from a few clients that saw v1.0 (however no proper testing were utilized to collect feedback)
















